Access Control Systems Security Identity Management And Trust Models
[PDF] Access Control Systems Security Identity Management And Trust Models Ebook
Nerc Cip Compliance Defining Your Electronic Security
Nerc Cip Compliance Defining Your Electronic Security

End To End Security Management For The Iot
End To End Security Management For The Iot

Gartner Magic Quadrant Mq Datarobot
Gartner Magic Quadrant Mq Datarobot
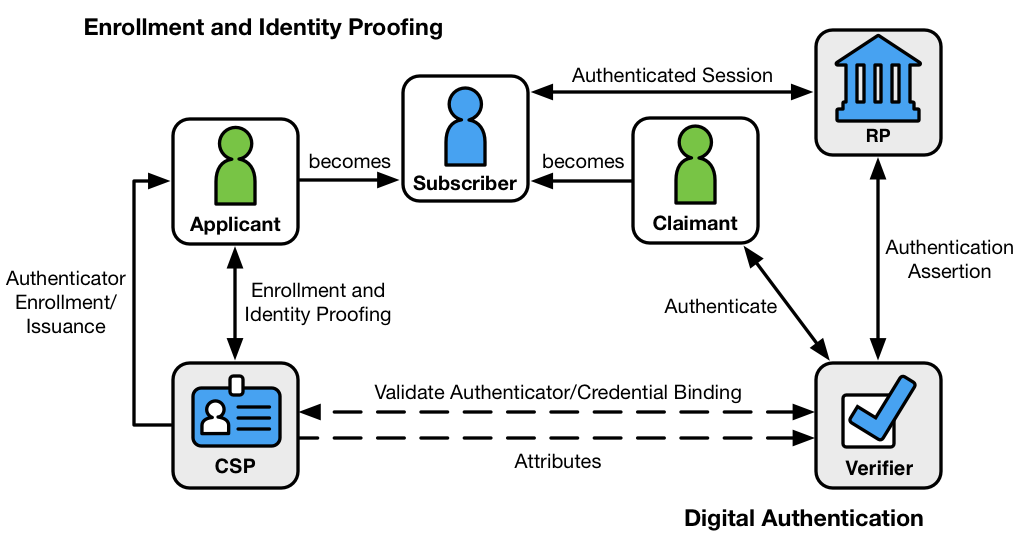
Nist Special Publication 800 63 3
Nist Special Publication 800 63 3

0 Response to "Access Control Systems Security Identity Management And Trust Models"
Post a Comment