Securing Business Information Strategies To Protect The Enterprise And Its Network IT Best Practices Series
[PDF] Securing Business Information Strategies To Protect The Enterprise And Its Network IT Best Practices Series Ebook
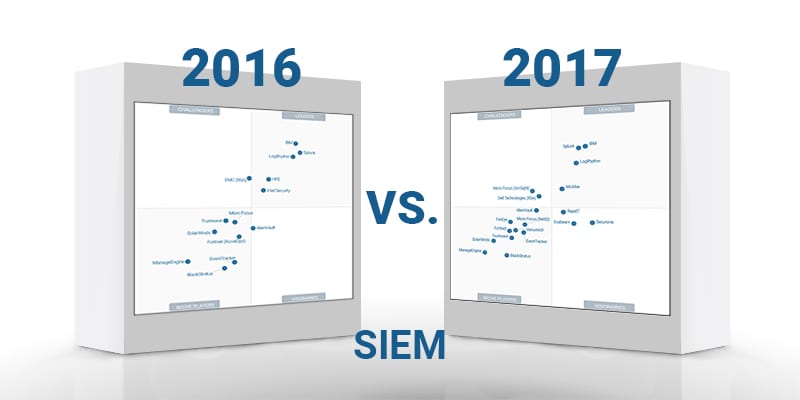
What S Changed Gartner S 2017 Siem Magic Quadrant

Top 10 Endpoint Security Providers In The Cybersecurity
Securing Active Directory: An Overview of Best Practices To learn more about the best practices that support these strategies, refer to "Best Practices for Securing Active Directory." Identifying Vulnerabilities. Most IT security breaches start with the compromise of only one or two computers within an infrastructure. Beyond these entry points, the progress of the breach can spread quickly. 10 Cybersecurity Best Practices for IT, IS, Network & Data ... Editor s Note: We ve created a 2019 cybersecurity predictions and a 2019 cybersecurity best practices post for the most up-to-date information. The following post has not been updated since it s original posting in 2017. Everyone wishes their organization could be more secure. Most security professionals agree that it is not a matter of if you get breached it s a matter of when. Enterprise information security architecture - Wikipedia Enterprise information security architecture (EISA) is the practice of applying a comprehensive and rigorous method for describing a current and/or future structure and behavior for an organization's security processes, information security systems, personnel and organizational sub-units, so that they align with the organization's core goals and strategic direction.
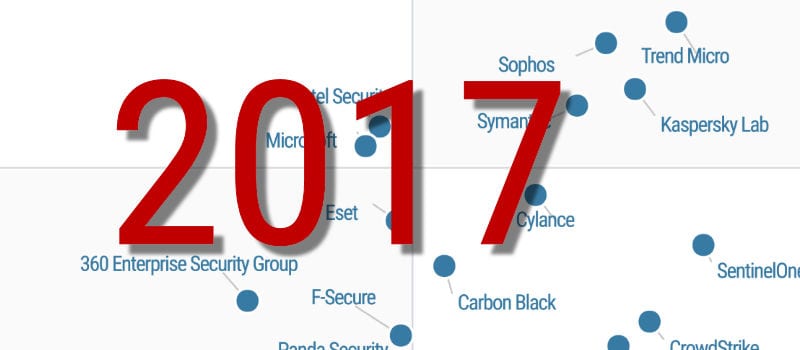
Gartner S 2017 Magic Quadrant For Endpoint Protection
Ulf Mattsson Cto Protegrity Ppt Download
Information And Data Management The Mitre Corporation

0 Response to "Securing Business Information Strategies To Protect The Enterprise And Its Network IT Best Practices Series"
Post a Comment